Legacy Offered APIs¶
Warning
These Legacy APIs are scheduled to be deprecated after the Frankfurt release!
The Policy subsystem of ONAP maintains, distributes, and operates on the set of rules that underlie ONAP’s control, orchestration, and management functions. Policy provides a centralized environment for the creation and management of easily-updatable conditional rules. It enables users to validate policies and rules, identify and resolve overlaps and conflicts, and derive additional policies where needed. The following operations are supported by the policy API:
Create policies on the PAP
Update policies on the PAP
Delete policies on the PAP or PDP
Push policies from the PAP to the PDP
List policies on the PDP
Get config data of policies on the PDP
Create Dictionary Items
Update Dictionary Items
Retrieve Dictionary Items
Import Micro Services Models
Retrieve Metrics for policy counts from PDP and PAP
POLICY Engine Services¶
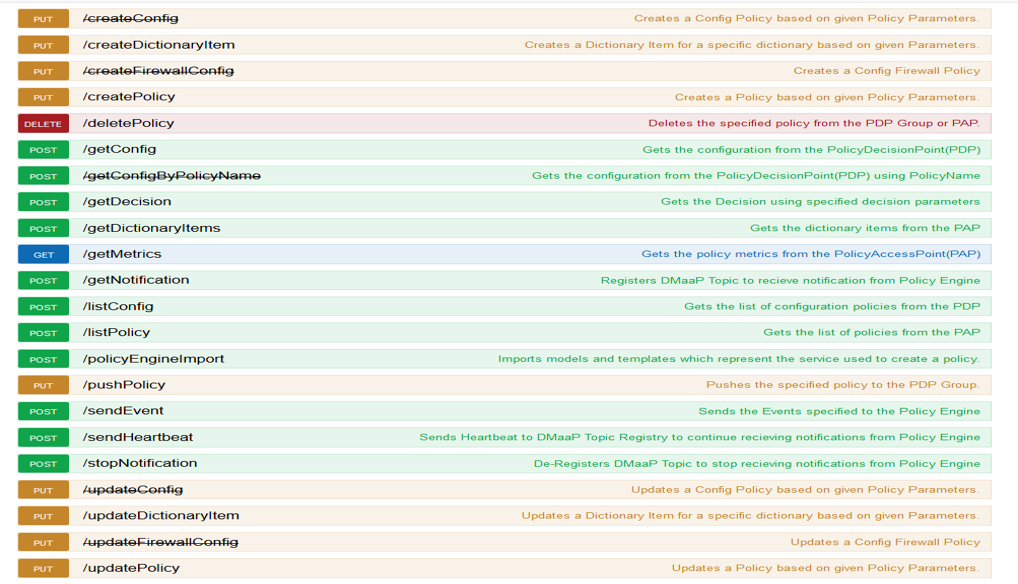
POLICY API Details¶
policy-engine-services¶
PUT /createConfig
Creates a Config Policy based on given Policy Parameters.
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
configPolicyAPIRequest |
body |
configPolicyAPIRequest |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
PUT /createDictionaryItem
Creates a Dictionary Item for a specific dictionary based on given Parameters.
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
dictionaryParameters |
body |
dictionaryParameters |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
PUT /createFirewallConfig
Creates a Config Firewall Policy
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
configFirewallPolicyAPIRequest |
body |
configFirewallPolicyAPIRequest |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
PUT /createPolicy
Creates a Policy based on given Policy Parameters.
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
policyParameters |
body |
policyParameters |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
DELETE /deletePolicy
Deletes the specified policy from the PDP Group or PAP.
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
deletePolicyParameters |
body |
deletePolicyParameters |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
401 - Unauthorized
204 - No Content
403 - Forbidden
POST /getConfig
Gets the configuration from the PolicyDecisionPoint(PDP)
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
configRequestParameters |
body |
configRequestParameters |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
POST /getConfigByPolicyName
Gets the configuration from the PolicyDecisionPoint(PDP) using PolicyName
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
configNameRequest |
body |
configNameRequest |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
POST /getDecision
Gets the Decision using specified decision parameters
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
decisionRequestParameters |
body |
decisionRequestParameters |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
POST /getDictionaryItems
Gets the dictionary items from the PAP
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
dictionaryParameters |
body |
dictionaryParameters |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
GET /getMetrics
Gets the policy metrics from the PolicyAccessPoint(PAP)
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
401 - Unauthorized
403 - Forbidden
404 - Not Found
POST /getNotification
Registers DMaaP Topic to recieve notification from Policy Engine
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
notificationTopic |
body |
notificationTopic |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
POST /listConfig
Gets the list of configuration policies from the PDP
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
configRequestParameters |
body |
configRequestParameters |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
POST /listPolicy
Gets the list of policies from the PDP
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
configNameRequest |
body |
configNameRequest |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
POST /policyEngineImport
Imports Policy based on the parameters which represent the service used to create a policy Service.
Consumes: [‘multipart/form-data’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
importParametersJson |
query |
importParametersJson |
string |
file |
formData |
file |
file |
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
PUT /pushPolicy
Pushes the specified policy to the PDP Group.
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
pushPolicyParameters |
body |
pushPolicyParameters |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
POST /sendEvent
Sends the Events specified to the Policy Engine
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
eventRequestParameters |
body |
eventRequestParameters |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
POST /sendHeartbeat
Sends Heartbeat to DMaaP Topic Registry to continue recieving notifications from Policy Engine
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
notificationTopic |
body |
notificationTopic |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
POST /stopNotification
De-Registers DMaaP Topic to stop recieving notifications from Policy Engine
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
notificationTopic |
body |
notificationTopic |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
PUT /updateConfig
Updates a Config Policy based on given Policy Parameters.
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
configPolicyAPIRequest |
body |
configPolicyAPIRequest |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
PUT /updateDictionaryItem
Updates a Dictionary Item for a specific dictionary based on given Parameters.
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
dictionaryParameters |
body |
dictionaryParameters |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
PUT /updateFirewallConfig
Updates a Config Firewall Policy
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
configFirewallPolicyAPIRequest |
body |
configFirewallPolicyAPIRequest |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
PUT /updatePolicy
Updates a Policy based on given Policy Parameters.
Consumes: [‘application/json’]
Produces: [‘*/*’]
Parameters
Name |
Position |
Description |
Type |
|---|---|---|---|
policyParameters |
body |
policyParameters |
|
ClientAuth |
header |
ClientAuth |
string |
X-ECOMP-RequestID |
header |
X-ECOMP-RequestID |
string |
Authorization |
header |
string |
|
Environment |
header |
string |
Responses
200 - OK
201 - Created
401 - Unauthorized
403 - Forbidden
404 - Not Found
Examples¶
SAMPLE JAVA CLIENT CODE
Get Config Example¶1 package org.onap.policyEngine; 2 3 import java.util.Collection; 4 5 import org.onap.policy.api.ConfigRequestParameters; 6 import org.onap.policy.api.PolicyConfig; 7 import org.onap.policy.api.PolicyEngine; 8 9 public class GetConfigSample { 10 11 public static void main(String[] args) throws Exception { 12 PolicyEngine pe = new PolicyEngine("config.properties"); 13 ConfigRequestParameters configRequestParams = new ConfigRequestParameters(); 14 configRequestParams.setPolicyName(".*"); 15 Collection<PolicyConfig> configs = pe.getConfig(configRequestParams); 16 for (PolicyConfig config: configs){ 17 System.out.println(config.getPolicyConfigMessage()); 18 System.out.println(config.getPolicyConfigStatus()); 19 } 20 } 21 }Create Config FIrewall Policy Example¶1 package org.onap.policyEngine; 2 3 import java.io.File; 4 import java.io.FileInputStream; 5 import java.io.FileNotFoundException; 6 import java.io.IOException; 7 import java.io.InputStream; 8 import java.io.StringReader; 9 import java.nio.file.Path; 10 import java.nio.file.Paths; 11 import java.text.SimpleDateFormat; 12 import java.util.Date; 13 import java.util.UUID; 14 15 import javax.json.Json; 16 import javax.json.JsonObject; 17 import javax.json.JsonReader; 18 19 import org.onap.policy.api.PolicyChangeResponse; 20 import org.onap.policy.api.PolicyConfigType; 21 import org.onap.policy.api.PolicyEngine; 22 import org.onap.policy.api.PolicyParameters; 23 import org.onap.policy.api.PolicyType; 24 25 public class ConfigFirewallPolicyClient { 26 static Boolean isEdit = false; 27 public static void main(String[] args) { 28 try{ 29 PolicyEngine policyEngine = new PolicyEngine("config.properties"); 30 PolicyParameters policyParameters = new PolicyParameters(); 31 // Set Policy Type 32 policyParameters.setPolicyConfigType(PolicyConfigType.Firewall); //required 33 policyParameters.setPolicyName("MikeAPItesting.testConfigFirewallPolicy1607_1"); //required 34 //policyParameters.setPolicyScope("MikeAPItesting"); 35 //Directory will be created where the Policies are saved... this displays a subscope on the GUI 36 policyParameters.setRequestID(UUID.randomUUID()); 37 38 // Set Safe Policy value for Risk Type 39 SimpleDateFormat dateformat3 = new SimpleDateFormat("dd/MM/yyyy"); 40 Date date = dateformat3.parse("15/10/2016"); 41 policyParameters.setTtlDate(date); 42 // Set Safe Policy value for Guard 43 policyParameters.setGuard(true); 44 // Set Safe Policy value for Risk Level 45 policyParameters.setRiskLevel("5"); 46 // Set Safe Policy value for Risk Type 47 policyParameters.setRiskType("PROD"); 48 File jsonFile = null; 49 String jsonRuleList = null; 50 Path file = Paths.get("C:\\policyAPI\\firewallRulesJSON\\Config_FW_Sample.json"); 51 jsonFile = file.toFile(); 52 53 //buildJSON(jsonFile, jsonRuleList); 54 policyParameters.setConfigBody(buildJSON(jsonFile, jsonRuleList).toString()); 55 policyParameters.setConfigBodyType(PolicyType.JSON); 56 // API method to create Policy or update policy 57 PolicyChangeResponse response = null; 58 if (!isEdit) { 59 response = policyEngine.createPolicy(policyParameters); 60 } else { 61 response = policyEngine.updatePolicy(policyParameters); 62 } 63 64 if(response.getResponseCode()==200){ 65 System.out.println(response.getResponseMessage()); 66 System.out.println("Policy Created Successfully!"); 67 }else{ 68 System.out.println("Error! " + response.getResponseMessage()); 69 } 70 } catch (Exception e) { 71 System.err.println(e.getMessage()); 72 } 73 74 } 75 76 private static JsonObject buildJSON(File jsonInput, String jsonString) throws FileNotFoundException { 77 JsonObject json = null; 78 JsonReader jsonReader = null; 79 if (jsonString != null && jsonInput == null) { 80 StringReader in = null; 81 in = new StringReader(jsonString); 82 jsonReader = Json.createReader(in); 83 json = jsonReader.readObject(); 84 in.close(); 85 } else { 86 InputStream in = null; 87 in = new FileInputStream(jsonInput); 88 jsonReader = Json.createReader(in); 89 json = jsonReader.readObject(); 90 try { 91 in.close(); 92 } catch (IOException e) { 93 System.err.println("Exception Occured while closing input stream"+e); 94 } 95 } 96 jsonReader.close(); 97 return json; 98 } 99 100 }Sample JSON file - Config_FW_Sample.json¶1 { 2 "serviceTypeId": "/v0/firewall/pan", 3 "configName": "AFTTFwPolicy1Config", 4 "deploymentOption": { 5 "deployNow": false 6 }, 7 "securityZoneId": "cloudsite:dev1a", 8 "serviceGroups": [{ 9 "name": "SSH", 10 "description": "Ssh service entry in service list", 11 "type": "SERVICE", 12 "transportProtocol": "tcp", 13 "appProtocol": null, 14 "ports": "22" 15 }], 16 "addressGroups": [{ 17 "name": "CiscoVCE", 18 "description": "Destination CiscoCVE", 19 "members": [{ 20 "type": "SUBNET", 21 "value": "12.63.31.61/12" 22 }] 23 }, { 24 "name": "HOHOServers", 25 "description": "Source HOHOServers for first testing", 26 "members": [{ 27 "type": "SUBNET", 28 "value": "12.60.32.11/23" 29 }] 30 }], 31 "firewallRuleList": [{ 32 "position": "1", 33 "ruleName": "FWRuleHOHOServerToCiscoVCE", 34 "fromZones": ["UntrustedZoneCiscoCVEName"], 35 "toZones": ["TrustedZoneHOHOName"], 36 "negateSource": false, 37 "negateDestination": false, 38 "sourceList": [{ 39 "type": "REFERENCE", 40 "name": "HOHOServers" 41 }], 42 "destinationList": [{ 43 "type": "REFERENCE", 44 "name": "CiscoVCE" 45 }], 46 "sourceServices": [], 47 "destServices": [{ 48 "type": "REFERENCE", 49 "name": "SSH" 50 }], 51 "action": "accept", 52 "description": "FW rule for HOHO source to CiscoVCE destination", 53 "enabled": true, 54 "log": true 55 }] 56 }Delete Policy Example¶1 package org.onap.policyEngine; 2 3 import org.onap.policy.api.DeletePolicyCondition; 4 import org.onap.policy.api.DeletePolicyParameters; 5 import org.onap.policy.api.PolicyChangeResponse; 6 import org.onap.policy.api.PolicyEngine; 7 8 public class DeletePolicyClient { 9 10 public static void main(String[] args) { 11 try { 12 13 PolicyEngine policyEngine = new PolicyEngine("config.properties"); 14 DeletePolicyParameters policyParameters = new DeletePolicyParameters(); 15 16 //Parameter arguments 17 policyParameters.setPolicyName("MikeConsole.Config_testDeleteAPI6.1.xml"); 18 policyParameters.setPolicyComponent("PDP"); 19 policyParameters.setPdpGroup("default"); 20 policyParameters.setDeleteCondition(DeletePolicyCondition.ALL); 21 policyParameters.setRequestID(null); 22 23 // API method to Push Policy to PDP 24 PolicyChangeResponse response = null; 25 response = policyEngine.deletePolicy(policyParameters); 26 27 if(response.getResponseCode()==200){ 28 System.out.println(response.getResponseMessage()); 29 System.out.println("Policy Deleted Successfully!"); 30 }else{ 31 System.out.println("Error! " + response.getResponseMessage()); 32 } 33 34 } catch (Exception e) { 35 System.err.println(e.getMessage()); 36 37 } 38 } 39 }Push Policy Example¶1 package org.onap.policyEngine; 2 3 import org.onap.policy.api.PolicyChangeResponse; 4 import org.onap.policy.api.PolicyEngine; 5 import org.onap.policy.api.PushPolicyParameters; 6 7 public class PushPoliciesToPDP { 8 public static void main(String[] args) { 9 try { 10 11 PolicyEngine policyEngine = new PolicyEngine("config.properties"); 12 PushPolicyParameters policyParameters = new PushPolicyParameters(); 13 14 //Parameter arguments 15 policyParameters.setPolicyName("Mike.testCase1"); 16 policyParameters.setPolicyType("Base"); 17 //policyParameters.setPolicyScope("MikeAPItesting"); 18 policyParameters.setPdpGroup("default"); 19 policyParameters.setRequestID(null); 20 21 // API method to Push Policy to PDP 22 PolicyChangeResponse response = null; 23 response = policyEngine.pushPolicy(policyParameters); 24 25 if(response.getResponseCode()==204){ 26 System.out.println(response.getResponseMessage()); 27 System.out.println("Policy Pushed Successfully!"); 28 }else{ 29 System.out.println("Error! " + response.getResponseMessage()); 30 } 31 32 } catch (Exception e) { 33 System.err.println(e.getMessage()); 34 35 } 36 } 37 }Decision Policy Example¶1 package org.onap.policyEngine; 2 3 import java.util.Arrays; 4 import java.util.HashMap; 5 import java.util.LinkedList; 6 import java.util.List; 7 import java.util.Map; 8 import java.util.UUID; 9 10 import org.onap.policy.api.AttributeType; 11 import org.onap.policy.api.PolicyChangeResponse; 12 import org.onap.policy.api.PolicyClass; 13 import org.onap.policy.api.PolicyEngine; 14 import org.onap.policy.api.PolicyParameters; 15 16 public class DecisionPolicyClient { 17 static Boolean isEdit = true; 18 public static void main(String[] args) { 19 try { 20 PolicyEngine policyEngine = new PolicyEngine("config.properties"); 21 PolicyParameters policyParameters = new PolicyParameters(); 22 // Set Policy Type 23 policyParameters.setPolicyClass(PolicyClass.Decision); //required 24 policyParameters.setPolicyName("MikeAPItests.testDecisionAPI"); //required 25 policyParameters.setOnapName("java"); //required 26 policyParameters.setPolicyDescription("This is a sample Decision policy UPDATE example with Settings"); //optional 27 //policyParameters.setPolicyScope("MikeAPItests"); 28 //Directory will be created where the Policies are saved... this 29 displays a a subscope on the GUI 30 31 //Set the Component Attributes... These are Optional 32 Map<String, String> configAttributes = new HashMap<>(); 33 configAttributes.put("Template", "UpdateTemplate"); 34 configAttributes.put("controller", "default"); 35 configAttributes.put("SamPoll", "30"); 36 configAttributes.put("value", "abcd"); 37 38 Map<AttributeType, Map<String,String>> attributes = new HashMap<>(); 39 attributes.put(AttributeType.MATCHING, configAttributes); 40 41 //Set the settings... These are Optional 42 Map<String, String> settingsMap = new HashMap<>(); 43 settingsMap.put("server", "5"); 44 45 attributes.put(AttributeType.SETTINGS, settingsMap); 46 policyParameters.setAttributes(attributes); 47 48 49 List<String> dynamicRuleAlgorithmLabels = new LinkedList<>(); 50 List<String> dynamicRuleAlgorithmFunctions = new LinkedList<>(); 51 List<String> dynamicRuleAlgorithmField1 = new LinkedList<>(); 52 List<String> dynamicRuleAlgorithmField2 = new LinkedList<>(); 53 54 //Example of a complex Rule algorithm using the settings in the Field1 55 /* label field1 function field2 56 * ***************************************************** 57 * A1 S_server integer-equal 90 58 * A2 cap string-contains ca 59 * A3 cobal integer-equal 90 60 * A4 A2 and A3 61 * A5 Config integer-greater-than 45 62 * A6 A4 ` or A5 63 * A7 A1 and A6 64 */ 65 dynamicRuleAlgorithmLabels = Arrays.asList("A1","A2","A3","A4","A5","A6","A7"); 66 dynamicRuleAlgorithmField1 = Arrays.asList("S_server","cap","cobal","A2","Config","A4","A1"); 67 dynamicRuleAlgorithmFunctions = Arrays.asList("integer-equal","string-contains","integer-equal","and","integer-greater-than","or","and"); 68 dynamicRuleAlgorithmField2 = Arrays.asList("90","ca","90","A3","45","A5","A6"); 69 70 policyParameters.setDynamicRuleAlgorithmLabels(dynamicRuleAlgorithmLabels); 71 policyParameters.setDynamicRuleAlgorithmField1(dynamicRuleAlgorithmField1); 72 policyParameters.setDynamicRuleAlgorithmFunctions(dynamicRuleAlgorithmFunctions); 73 policyParameters.setDynamicRuleAlgorithmField2(dynamicRuleAlgorithmField2); 74 75 policyParameters.setRequestID(UUID.randomUUID()); 76 77 // API method to create Policy or update policy 78 PolicyChangeResponse response = null; 79 if (!isEdit) { 80 response = policyEngine.createPolicy(policyParameters); 81 } else { 82 response = policyEngine.updatePolicy(policyParameters); 83 } 84 85 if(response.getResponseCode()==200){ 86 System.out.println(response.getResponseMessage()); 87 System.out.println("Policy Created Successfully!"); 88 }else{ 89 System.out.println("Error! " + response.getResponseMessage()); 90 } 91 } catch (Exception e) { 92 System.err.println(e.getMessage()); 93 } 94 } 95 }ListPolicy Example¶1package org.onap.policyengine; 2 3import java.util.Collection; 4import org.onap.policy.api.ConfigNameRequest; 5import org.onap.policy.api.PolicyEngine; 6 7/** 8 * List Policy Client Code 9 * policyName : ".*" returns list of policy names from PAP. 10 * policyName : "scope + "_" + "policyType" + "_" + policyName" + ".*" returns the matching policy from pap (active version) 11 * 12 */ 13 public class ListPolicyClient { 14 public static void main(String[] args) throws Exception { 15 PolicyEngine pe = new PolicyEngine("config.properties"); 16 ConfigNameRequest listPolicyParams = new ConfigNameRequest(); 17 listPolicyParams.setPolicyName(".*"); 18 Collection<String> policies = pe.listPolicy(listPolicyParams); 19 for (String policy : policies) { 20 System.out.println(policy); 21 } 22 } 23 }List Config Policy Example¶1 package org.onap.policyEngine; 2 3 import java.util.Collection; 4 import java.util.HashMap; 5 import java.util.Map; 6 import java.util.UUID; 7 8 import org.onap.policy.api.ConfigRequestParameters; 9 import org.onap.policy.api.PolicyConfigException; 10 import org.onap.policy.api.PolicyEngine; 11 import org.onap.policy.api.PolicyEngineException; 12 import org.onap.policy.common.logging.flexlogger.FlexLogger; 13 import org.onap.policy.common.logging.flexlogger.Logger; 14 15 public class ListConfigPoliciesClient { 16 17 private static final Logger LOGGER = FlexLogger.getLogger(ListConfigPoliciesClient.class); 18 19 public static void main(String[] args) { 20 PolicyEngine policyEngine; 21 22 // List Config Policies Example 23 try { 24 policyEngine = new PolicyEngine("config.properties"); 25 ConfigRequestParameters parameters = new ConfigRequestParameters(); 26 27 parameters.setPolicyName(".*"); 28 parameters.setOnapName(".*"); 29 parameters.setConfigName(".*"); 30 31 Map<String, String> configAttributes = new HashMap<>(); 32 configAttributes.put("java", "java"); 33 configAttributes.put("peach", "Tar"); 34 configAttributes.put("true", "false"); 35 configAttributes.put("small", "testPass"); 36 parameters.setConfigAttributes(configAttributes); 37 38 parameters.setRequestID(UUID.randomUUID()); 39 40 Collection<String> response = policyEngine.listConfig(parameters); 41 if(response!=null && !response.contains("PE300")){ 42 for(String configList : response){ 43 System.out.println(configList.toString()+"\n"); 44 } 45 }else{ 46 System.out.println("Error! " +response); 47 } 48 49 } catch (PolicyConfigException e) { 50 LOGGER.error("Exception Occured"+e); 51 } catch (PolicyEngineException e) { 52 LOGGER.error("Exception Occured"+e); 53 } 54 } 55 }
JSON EXAMPLES
Create Microservice Policy¶1 API: createPolicy 2 OPERATION: PUT 3 REQUEST BODY: 4 { 5 "configBody": "{ 6 \"service\":\"ControllerServiceSampleSdnlServiceInstance\", 7 \"location\":\"Edge\", 8 \"uuid\":\"TestUUID\", 9 \"policyName\":\"testRestCreateMicroServicesNewParams\", 10 \"description\":\"testing Create\", 11 \"configName\":\"TestName\", 12 \"templateVersion\":\"1604\", 13 \"priority\":\"4\", 14 \"version\":\"0.1.0-SNAPSHOT\", 15 \"policyScope\":\"resource=F5,service=vSCP,type=configuration,closedLoopControlName=vSCP_F5_Firewall_d925ed73-8231-4d02-9545-db4e101f88f8\", 16 \"content\":{ 17 \"taskOrchestratedConfiguration\":\"test\", 18 \"taskCustomConfiguration\":\"set\", 19 \"configuration\":\"test\", 20 \"cdapUrl\":\"testurl\", 21 \"taskName\":\"test\", 22 \"taskNameTEST\":\"TEST\", 23 \"users\":\"[tuser]\", 24 \"adminUsers\":\"[lji]\", 25 \"taskConfigFilePath\":\"test\", 26 \"managerPortNumber\":\"999\", 27 \"taskType\":\"test\", 28 \"taskCommandFilePath\":\"tset\", 29 \"contailIp\":\"test\", 30 \"consoleUsers\":\"[odu-e2e]\", 31 \"taskStatusFilePath\":\"test\" 32 } 33 }", 34 "policyConfigType": "MicroService", 35 "policyName": "MikeAPITesting.testRestCreateMicroServicesNewParams", 36 "ecompName": "SDNC" 37 }Update Microservice Policy¶1 API: updatePolicy 2 OPERATION: PUT 3 REQUEST BODY: 4 { 5 "configBody": "{ 6 \"service\":\"ControllerServiceSampleSdnlServiceInstance\", 7 \"location\":\"Edge\", 8 \"uuid\":\"TestUUID\", 9 \"policyName\":\"testRestCreateMicroServicesNewParams\", 10 \"description\":\"testing Update\", 11 \"configName\":\"TestName\", 12 \"templateVersion\":\"1604\", 13 \"priority\":\"4\", 14 \"version\":\"0.1.0-SNAPSHOT\", 15 \"policyScope\":\"resource=F5,service=vSCP,type=configuration,closedLoopControlName=vSCP_F5_Firewall_d925ed73-8231-4d02-9545-db4e101f88f8\", 16 \"content\":{ 17 \"taskOrchestratedConfiguration\":\"test\", 18 \"taskCustomConfiguration\":\"set\", 19 \"configuration\":\"test\", 20 \"cdapUrl\":\"testurl\", 21 \"taskName\":\"test\", 22 \"taskNameTEST\":\"TEST\", 23 \"users\":\"[tuser]\", 24 \"adminUsers\":\"[lji]\", 25 \"taskConfigFilePath\":\"test\", 26 \"managerPortNumber\":\"999\", 27 \"taskType\":\"test\", 28 \"taskCommandFilePath\":\"tset\", 29 \"contailIp\":\"test\", 30 \"consoleUsers\":\"[odu-e2e]\", 31 \"taskStatusFilePath\":\"test\" 32 } 33 }", 34 "policyConfigType": "MicroService", 35 "policyName": "MikeAPITesting.testRestUpdateMicroServicesNewParams", 36 "ecompName": "SDNC" 37 }
CURL EXAMPLES
Push Policy¶echo "pushPolicy : PUT : com.vLoadBalancer" echo "pushPolicy : PUT : com.vLoadBalancer" curl -v --silent -X PUT --header 'Content-Type: application/json' --header 'Accept: text/plain' --header 'ClientAuth: XYZ' --header 'Authorization: Basic XYZ' --header 'Environment: TEST' -d '{ "pdpGroup": "default", "policyName": "com.vLoadBalancer", "policyType": "MicroService" }' 'http://pdp:8081/pdp/api/pushPolicy'Delete Policy¶echo "deletePolicy : DELETE : com.vFirewall" curl -v --silent -X DELETE --header 'Content-Type: application/json' --header 'Accept: text/plain' --header 'ClientAuth: XYZ' --header 'Authorization: Basic XYZ' --header 'Environment: TEST' -d '{ "pdpGroup": "default", "policyComponent": "PDP", "policyName": "com.vFirewall", "policyType": "MicroService" }' 'http://pdp:8081/pdp/api/deletePolicy'Get Config¶echo "Get all Config Policy example" curl -i -v -H 'Content-Type: application/json' -H 'Accept: application/json' -H 'ClientAuth: XYZ' -H 'Authorization: Basic XYZ -H 'Environment: TEST' -X POST -d '{ "policyName": ".*" }' http://${PDP_IP}:8081/pdp/api/getConfig
ADDITIONAL EXAMPLES
Deleting a Policy from PAP¶// Deleting from PAP will remove the policy from the PolicyEntity & PolicyVersion tables (UI-Editor tab). // This means that the policy is no longer be available in Policy System. // PayLoad: { "policyName": "com.testpolicy", //scope.policyName "policyType": "Base", //policy type "policyComponent": "PAP", //component name "deleteCondition": "ALL" //versions (ALL or CURRENT) }Deleting a Policy from PDP¶// Deleting from PDP will delete the policy from the PDP Group. The policy is still available in Policy System. // When the policy is needed again, the policy should be pushed to the PDP. // PayLoad: { "policyName": "com.testpolicy", //scope.policyName "policyType": "Base", //policy type "policyComponent": "PDP", //component name "pdpGroup": "Default" //group name }
End of Document