OOM Optional Addons
The following optional applications can be added to your kubernetes environment.
Install Prometheus Stack
Prometheus is an open-source systems monitoring and alerting toolkit with an active ecosystem.
Kube Prometheus Stack is a collection of Kubernetes manifests, Grafana dashboards, and Prometheus rules combined with documentation and scripts to provide easy to operate end-to-end Kubernetes cluster monitoring with Prometheus using the Prometheus Operator. As it includes both Prometheus Operator and Grafana dashboards, there is no need to set up them separately. See the Prometheus stack README for more information.
To install the prometheus stack, execute the following:
Add the prometheus-community Helm repository:
> helm repo add prometheus-community https://prometheus-community.github.io/helm-charts
Update your local Helm chart repository cache:
> helm repo update
To install prometheus, execute the following, replacing the <recommended-pm-version> with the version defined in the OOM Software Requirements (base) table:
> helm install prometheus prometheus-community/kube-prometheus-stack --namespace=prometheus --create-namespace --version=<recommended-pm-version>
ONAP on Service Mesh
Warning
“ONAP on Service Mesh” is not fully supported in “Kohn”. Full support is planned for London release to support the ONAP Next Generation Security & Logging Structure
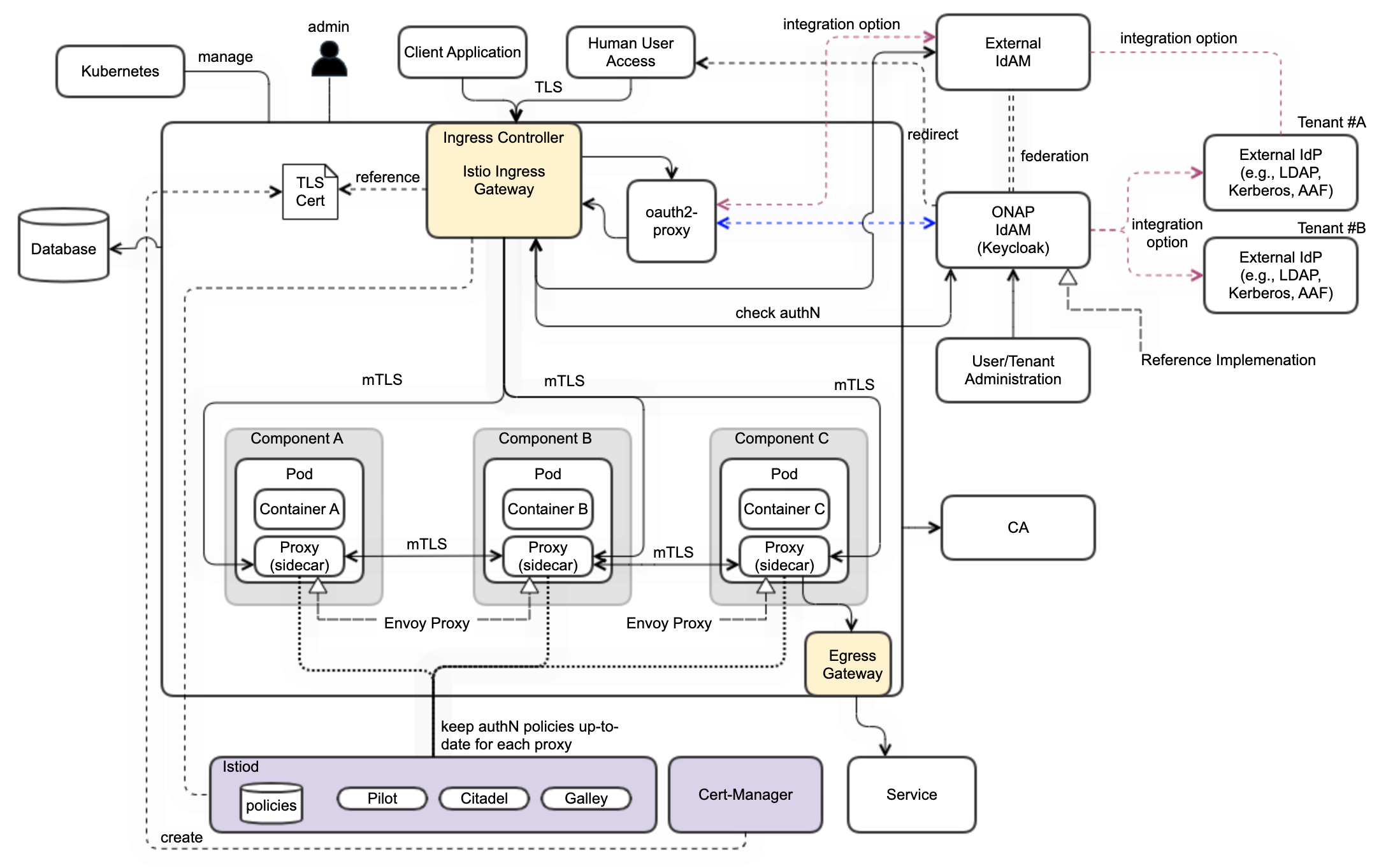
ONAP is currenty planned to support Istio as default ServiceMesh platform. Therefor the following instructions describe the setup of Istio and required tools. Used Istio best practices and Istio setup guide
Istio Platform Installation
Install Istio Basic Platform
Configure the Helm repository:
> helm repo add istio https://istio-release.storage.googleapis.com/charts > helm repo update
Create a namespace for “mesh-level” configurations:
> kubectl create namespace istio-config
Create a namespace istio-system for Istio components:
> kubectl create namespace istio-system
Install the Istio Base chart which contains cluster-wide resources used by the Istio control plane, replacing the <recommended-istio-version> with the version defined in the OOM Software Requirements (base) table:
> helm upgrade -i istio-base istio/base -n istio-system --version <recommended-istio-version>
Install the Istio Base Istio Discovery chart which deploys the istiod service, replacing the <recommended-istio-version> with the version defined in the OOM Software Requirements (base) table (enable the variable to enforce the (sidecar) proxy startup before the container start):
> helm upgrade -i istiod istio/istiod -n istio-system --version <recommended-istio-version> --wait --set global.proxy.holdApplicationUntilProxyStarts=true --set meshConfig.rootNamespace=istio-config
Add an EnvoyFilter for HTTP header case
When handling HTTP/1.1, Envoy will normalize the header keys to be all lowercase. While this is compliant with the HTTP/1.1 spec, in practice this can result in issues when migrating existing systems that might rely on specific header casing. In our case a problem was detected in the SDC client implementation, which relies on uppercase header values. To solve this problem in general we add a EnvoyFilter to keep the uppercase header in the istio-config namespace to apply for all namespaces, but set the context to SIDECAR_INBOUND to avoid problems in the connection between Istio-Gateway and Services
Create a EnvoyFilter file (e.g. envoyfilter-case.yaml)
envoyfilter-case.yaml
apiVersion: networking.istio.io/v1alpha3 kind: EnvoyFilter metadata: name: header-casing namespace: istio-config spec: configPatches: - applyTo: CLUSTER match: context: SIDECAR_INBOUND patch: operation: MERGE value: typed_extension_protocol_options: envoy.extensions.upstreams.http.v3.HttpProtocolOptions: '@type': type.googleapis.com/envoy.extensions.upstreams.http.v3.HttpProtocolOptions use_downstream_protocol_config: http_protocol_options: header_key_format: stateful_formatter: name: preserve_case typed_config: '@type': type.googleapis.com/envoy.extensions.http.header_formatters.preserve_case.v3.PreserveCaseFormatterConfig - applyTo: NETWORK_FILTER match: listener: filterChain: filter: name: envoy.filters.network.http_connection_manager patch: operation: MERGE value: typed_config: '@type': type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager http_protocol_options: header_key_format: stateful_formatter: name: preserve_case typed_config: '@type': type.googleapis.com/envoy.extensions.http.header_formatters.preserve_case.v3.PreserveCaseFormatterConfig
Apply the change to Istio:
> kubectl apply -f envoyfilter-case.yaml
Install Istio Gateway
Create a namespace istio-ingress for the Istio Ingress gateway and enable istio-injection:
> kubectl create namespace istio-ingress > kubectl label namespace istio-ingress istio-injection=enabled
Install the Istio Gateway chart,replacing the <recommended-istio-version> with the version defined in the OOM Software Requirements (base) table:
> helm upgrade -i istio-ingressgateway istio/gateway -n istio-ingress --version <recommended-istio-version> --wait
Kiali Installation
Kiali is used to visualize the Network traffic in a ServiceMesh enabled cluster For setup the kiali operator is used, see Kiali setup guide
Install kiali-operator namespace:
> kubectl create namespace kiali-operator > kubectl label namespace kiali-operator istio-injection=enabled
Install the kiali-operator:
> helm repo add kiali https://kiali.org/helm-charts > helm repo update kiali > helm install --namespace kiali-operator kiali/kiali-operator
Create Kiali CR file (e.g. kiali.yaml)
kiali.yaml
apiVersion: kiali.io/v1alpha1 kind: Kiali metadata: name: kiali namespace: istio-system annotations: ansible.operator-sdk/verbosity: "1" spec: auth: strategy: anonymous istio_component_namespaces: prometheus: monitoring external_services: grafana: in_cluster_url: http://prometheus-stack-grafana.monitoring prometheus: url: http://prometheus-stack-kube-prom-prometheus.monitoring:9090 tracing: in_cluster_url: http://istio-query.observability:16686 deployment: accessible_namespaces: ["**"] view_only_mode: false server: web_root: "/kiali"
Install kiali:
> kubectl apply -f kiali.yaml
Create Ingress gateway entry for the kiali web interface using the configured Ingress <base-url> (here “simpledemo.onap.org”) as described in OOM Custom Overrides
kiali-ingress.yaml
apiVersion: networking.istio.io/v1beta1 kind: Gateway metadata: name: kiali-gateway spec: selector: istio: ingressgateway servers: - hosts: - kiali.simpledemo.onap.org port: name: http number: 80 protocol: HTTP --- apiVersion: networking.istio.io/v1beta1 kind: VirtualService metadata: name: kiali-service spec: hosts: - kiali.simpledemo.onap.org gateways: - kiali-gateway http: - route: - destination: port: number: 20001 host: kiali
Add the Ingress entry for Kiali:
> kubectl -n istio-system apply -f kiali-ingress.yaml
Jaeger Installation
To be done…